Host Booter Xr 2 1 Legit Copy And Paste
How can I configure puppet to provision a user on the guest machine with a username that matches the username of the user on the host machine who provisions the guest? (Using puppet apply, not server/master) $ puppet -version 3.4.3 $ vagrant -version Vagrant 1.7.2 This is what I've tried so far.
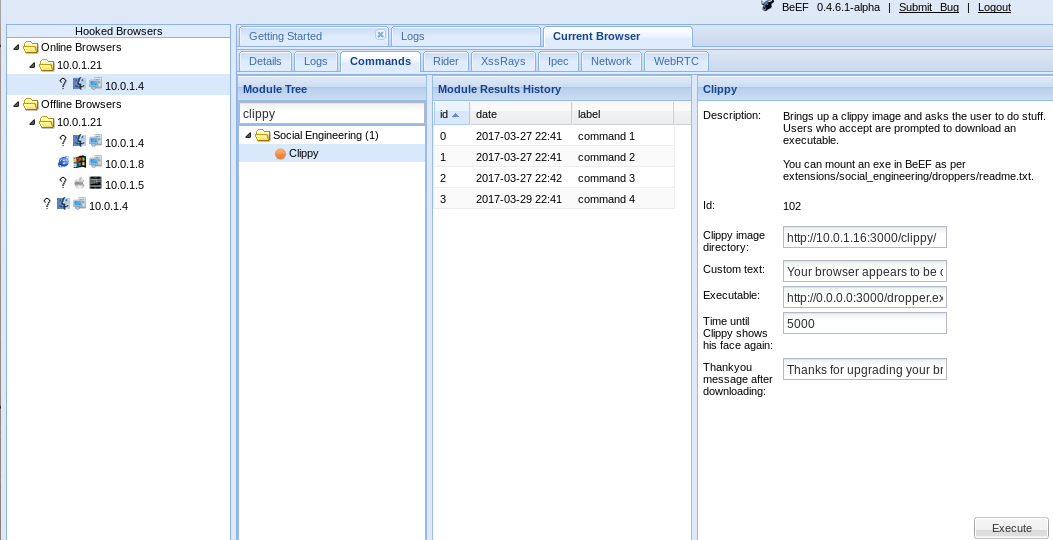
I am learning how to use htaccess.
First I want to try how to set up username and password for thefollowing directory
~/public_html/55/m:I manually created two text files:
.htaccessand.htpasswd.Their contents areBut I can access the webpage without being asked to provide usernameand password. I wonder why?
Second I want to try how to restrict the ip range to access
~/public_html/55/nwhere I created manually the text file
.htaccesswhose content is:But I can access the webpage from outside the specified ip range
xxx.edu. I wonder why?
Thanks and regards!
TimTim1 Answer
Maybe .htaccess files for those directories are simply ignored using the AllowOverride directive in the virtual host configuration. From http://httpd.apache.org/docs/2.2/mod/core.html#allowoverride:
When this directive is set to None, then .htaccess files are completely ignored. In this case, the server will not even attempt to read .htaccess files in the filesystem.
EDIT: On Ubuntu configuration is based in /etc/apache2, other systems have their configuration based in /etc/httpd or another directory. The Ubuntu configuration for user home directories is handled by mods-available/userdir.conf which is enabled when linked into /etc/apache2/mods-enabled. It specifies home directories as /home/*/public_html. The php4.conf also references the same directories.
Not the answer you're looking for? Browse other questions tagged permissions.htaccess or ask your own question.
On Monday, I profiled asylumbooter.com, one of several increasingly public DDoS-for-hire services posing as Web site “stress testing” services. Today, we’ll look at ragebooter.net, yet another attack service except for one secret feature which sets it apart from the competition: According the site’s proprietor, ragebooter.net includes a hidden backdoor that lets the FBI monitor customer activity.
This bizarre story began about a week ago, when I first started trying to learn who was responsible for running RageBooter. In late March, someone hacked and leaked the users table for ragebooter.net. The database showed that the very first user registered on the site picked the username “Justin,” and signed up with the email address “primalpoland@gmail.com.”
That email address is tied to a now-defunct Facebook account for 22-year-old Justin Poland from Memphis, Tenn. Poland’s personal Facebook account used the alias “PRIMALRAGE,” and was connected to a Facebook page for an entity called Rage Productions. Shortly after an interview with KrebsOnSecurity, Poland’s personal Facebook page was deleted, and his name was removed from the Rage Productions page.
Ragebooter.net’s registration records are hidden behind WHOIS privacy protection services. But according to a historic WHOIS lookup at domaintools.com, that veil of secrecy briefly fell away when the site was moved behind Cloudflare.com, a content distribution network that also protects sites against DDoS attacks like the ones Ragebooter and its ilk help to create (as I noted in Monday’s story, some of the biggest targets of booter services are in fact other booter services). For a brief period in Oct. 2012, the WHOIS records showed that ragebooter.net was registered by a Justin Poland in Memphis.
I “friended” Poland on Facebook and said I wanted to interview him. He accepted my request and sent me a chat to ask why I wanted to speak with him. I said I was eager to learn more about his business, and in particular why he thought it was okay to run a DDoS-for-hire service. While we were chatting, I took the liberty of perusing his profile pictures, which included several of a large tattoo he’d had inked across the top of his back — “Primal Rage” in a typeface fashioned after the text used in the Transformers movie series.
Poland is serious about his business.
“Since it is a public service on a public connection to other public servers this is not illegal,” Poland explained, saying that he’d even consulted with an attorney about the legality of his business. When I asked whether launching reflected DNS attacks was okay, Poland said his service merely took advantage of the default settings of some DNS servers.
“Nor is spoofing the sender address [illegal],” he wrote. “If the root user of the server does not want that used they can simple disable recursive DNS. My service is a legal testing service. How individuals use it is at there [sic] own risk and responsibilitys [sic]. I do not advertise this service anywhere nor do I entice or encourage illegal usage of the product. How the user uses it is at their own risk. I provide logs to any legal law enforcement and keep logs for up to 7 days.”
The conversation got interesting when I asked the logical follow-up question: Had the police or federal authorities ever asked for information about his customers?
That was when Poland dropped the bomb, informing me that he was actually working for the FBI.

“I also work for the FBI on Tuesdays at 1pm in memphis, tn,” Poland wrote. “They allow me to continue this business and have full access. The FBI also use the site so that they can moniter [sic] the activitys [sic] of online users.. They even added a nice IP logger that logs the users IP when they login.”
When I asked Poland to provide more information that I might use to verify his claims that he was working for the FBI, the conversation turned combative, and he informed me that I wasn’t allowed to use any of the information he’d already shared with me. I replied that I hadn’t and wouldn’t agree that any of our discussion was to be off the record, and he in turn promised to sue me if I ran this story. That was more or less the end of that conversation.
As to the relative legality of booter services, I consulted Mark Rasch, a security expert and former attorney for the U.S. Department of Justice. Rasch said companies hire stress testing services all the time, but usually as part of a more inclusive penetration testing engagement. In such engagements, Rasch said, it is common for the parties conducting the tests to insist upon and obtain beforehand a “get out of jail free card,” essentially a notarized letter from the customer stating that the testing firm was hired to break into and otherwise probe the security and stability of the targeted Web site.
“This is also why locksmiths generally force you to show ID that proves your address before they’ll break into a house for you,” Rasch said. “The standard in the security industry is not only to require proof that you own the sites that are going to be shut down or attacked, but also an indemnification provision.”
On Monday, I pinged Mr. Poland once more, again using Facebook’s chat function. I wanted to hear more about his claim that he was working for the feds. To my surprise, he gave me the number of a Memphis man he referred to as his FBI contact, a man Poland said he knew only as “Agent Lies.”
The man who answered at the phone number supplied by Poland declined to verify his name, seemed peeved that I’d called, and demanded to know who gave me his phone number. When I told him that I was referred to him by Mr. Poland, the person on the other end of the line informed me that he was not authorized to to speak with the press directly. He rattled off the name and number of the press officer in the FBI’s Memphis field office, and hung up.
Just minutes after I spoke with “Agent Lies,” Justin dropped me a line to say that he could not be my ‘friend’ any longer. “I have been asked to block you. Have a nice day,” Poland wrote in a Facebook chat, without elaborating. His personal Facebook page disappeared moments later.
Not long after that, I heard back from Joel Siskovic, spokesman for the Memphis FBI field office, who said he could neither confirm nor deny Poland’s claims. Siskovic also declined to verify whether the FBI had an Agent Lies.
“People come forward all the time and make claims they are working with us, and sometimes it’s true and sometimes it’s not,” Siskovic said. “But it wouldn’t be prudent for us to confirm that we have individuals helping us or assisting us, either because they’re being good citizens or because they’re somehow compelled to.”
Host Booter Xr 2 1 Legit Copy And Paste Jobs Online
Update, June 1: A little Googling shows that there is in fact an FBI Agent Lies in the Memphis area. Many of the public cases that Agent Lies has testified in appear to be child-exploitation related, such as this one (PDF).
Original post: I tried to imagine a scenario in which someone in Poland’s situation would make up a story like that, or — if the story were true — might be bold enough to brag about it. I went back over some of the screen shots I’d taken from Poland’s Facebook account before it was deleted, and discovered a saddening discussion where Poland says he is depressed because he can’t quit his habit of smoking marijuana incessantly. In one post he admits to spending more than $1,200 a week on pot. I’m not sure if $1,200 worth of weed is even humanly possible for one man to consume on his own in a week and still function, but it would certainly explain his erratic behavior. Anyway, apparently business is good.
I had a lot of help on this research from Brandon Levene and Allison Nixon, two security consultants who have been digging into the booter scene for some time now. Levene and Nixon said they happened on ragebooter.net after a generic search for other booters indicated it was one of the top three results.
“What made things interesting, however, were the top advertisements for this service from a forum poster using the name ‘Primal Rage,'” Levene said. “The contact information across multiple forums included the email Velocitypro@live.com, which tied to a [now-defunct] Facebook page for Velocity Production, and from this page we identified the private Facebook account of the owner, Justin Poland. Further research revealed more forum profiles using the name Primal Rage and another domain, Hybrid-host.com, registered to Justin Poland (polandjd@gmail.com).
Levene said the biggest break in their research came from a fawning post on a slightly less public site — leakforums.org — a forum dedicated to sharing information on, well, leaked forum databases for one thing. In a twist that makes this already odd story even weirder, Primal Rage/Justin says in his application for membership on leakforums.org that he is starting a new company called “Booter Be Gone,” which he said would be all about “leaking booters online and there [sic] databases.”
The short CV he posted to the leakforums application said he had experience as a computer repair technician and “Ddos mitigation specialist.” Translation: Eliminate the competition by leaking their databases, and then sell DDoS mitigation services to businesses besieged by attacks of the sort launched by his booter services. What could go wrong?
“Justin’s cross-contamination of online personas led me to dig deeper,” Levene said. “Simply by drawing focus he made himself a target. The whole thing with his service being for ‘legitimate stressing’ is silly. Even the news updates from the login panel are discussing ways to target users.”
Nixon said her research on ragebooter.net showed it to be a booter under active development and one that seems to average more than 400 attacks per day.
Ragebooter’s network structure. Image: Allison Nixon.
2 Equals 1
Oh, and that backdoor Poland claims he added for the FBI? Nixon may have found at least one of them:
“The booter has some information leakage problems too,” Nixon said. “The victims can see the ragebooter.net username of the logged in attacker because that info is, bizzarely, sent within attack traffic.”
The real irony of all this? Poland admitted in one of our Facebook chats that his own site was recently breached, leading to the leak of ragerbooter’s user database; the attackers broke into his Skype account, and then rifled through his Skype chats until they found login credentials to his servers. Was it the work of hackers allied with competing booter services? A spurned FBI agent? Or Justin himself? One thing’s for sure: If Poland’s “booter be gone” soon, it is nobody’s fault but his own.
One final note: Services like ragebooter.net would not be nearly as usable or profitable if they were unable to accept payment via PayPal. A Paypal spokesperson declined to comment on this particular booter service, but said the use of its service for DDoS-for-hire sites would violate its terms of use agreement.

“While we cannot share specifics on our customers’ accounts due to our privacy policy, we can confirm that we will review suspicious accounts for malicious activity and work with law enforcement to ensure cyber criminals are reported properly. We take security very seriously at PayPal and we do not condone the use of our site in the sale or dissemination of tools, which have the sole purpose to attack customers and illegally take down web sites.”
Tags: Allison Nixon, booter be gone, CloudFlare, fbi, Joel Siskovic, justin poland, leakforums.org, mark rasch, Memphis, Paypal, Rage Productions, ragebooter.net, Tenn.